Therefore, they are described in detail in the following table: To reinforce Authentication configuration, we will go through a few examples, illustrating the different ways in which Authentication can be configured in Cisco IOS software. Pearson Education, Inc., 221 River Street, Hoboken, New Jersey 07030, (Pearson) presents this site to provide information about Pearson IT Certification products and services that can be purchased through this site. These are described in the following table: The following example illustrates the configuration of a TACACS+ server using the IP address 10.1.1.254, with a pre-shared key of h0w2n3tw0rk and a timeout value of 15 seconds. This received username and encrypted password, as well as the NAS IP address and NAS port information, is sent as an Access-Request packet from the NAS to the RADIUS server, as illustrated in step 4. IT departments are responsible for managing many routers, switches, firewalls, and access points throughout a network. The third, and final, example demonstrates how to configure Authentication for all logins using a method list named LOGIN-LIST. TACACS+ server groups are configured via the aaa group server tacacs+ [name] global configuration command. 2023 Pearson Education, Pearson IT Certification. While these analytical services collect and report information on an anonymous basis, they may use cookies to gather web trend information. Use the tacacs-server key command to specify an encryption key to encrypt all exchanges between the NAS and the TACACS+ daemon. border patrol salary with military experience; lacounty holidays 2022; tacacs+ advantages and disadvantages. connection For outbound connections. Before we get into the specifics of RADIUS and TACACS+, let's define the different parts of AAA solutions. Participation is optional. Pearson collects information requested in the survey questions and uses the information to evaluate, support, maintain and improve products, services or sites; develop new products and services; conduct educational research; and for other purposes specified in the survey. You cannot have Authorization before Authentication. This keyword configures Accounting for all system-level events. What is TACACS+ Terminal Access Controller Access Control System (TACACS+) is Cisco proprietary protocol which is used for the communication of the Cisco ACS can be installed onto both Windows and Unix-based platforms. All TACACS+ packets will be sourced from the Loopback0 interface of the NAS: R1(config)#aaa group server tacacs+ IINS-TACACS, R1(config-sg-tacacs+)#server 172.31.1.254, R1(config-sg-tacacs+)#server 192.168.1.254, R1(config-sg-tacacs+)#ip tacacs source-interface loopback0. This data can indicate resource utilization, such as bandwidth and time used, and may be used for billing and/or security purposes. RADIUS communication is triggered by a user login that consists of a query. bandwidth, bytes used, etc.) [gravityform id="6" title="true" description="true"], Intrusion Detection and Prevention IDS/IPS, Why IT Security Certification Has Become a Must Have. This response is usually received when a communication problem exists between the NAS and the AAA server. TACACS+ was Cisco's response to RADIUS (circa 1996), handling what Cisco determined were some shortcomings in the RADIUS assumptions and design. However, these communications are not promotional in nature. Accounting is enabled for terminal lines via the accounting line configuration command and can also be enabled for certain WAN protocols (e.g. There are two basic types of method lists: Configure the security protocol parameters, such as the IP address and shared key, Define the Authentication service and the method lists, Apply the Authentication named method list(s) to interfaces or terminal lines, Apply the Authorization method list(s) to terminal lines, Define the Accounting service and method lists, Apply the Accounting method list(s) to terminal lines, RADIUS server parameters are configured by using the, TACACS+ server parameters are configured by using the, AAA server groups are configured by using the, Kerberos is a trusted third-party Authentication Layer 7 service, In the Kerberos protocol, the trusted third-party is the KDC, The Kerberos credential scheme uses a concept called single logon, Kerberos uses TCP/UDP ports 88, 543, 749 and TCP ports 754, 2105, and 444. unencrypted text. Authentication, Authorization, and Accounting, referred to as AAA (Triple-A), provide the framework that controls and monitors network access. on the NAS itself, or remotely, on a RADUIS, TACACS+ or Kerberos server, Unlike authentication and Authorization, there is no search for AV pairs in Accounting, RADIUS stands for Remote Authentication Dial-In User Service, The original specification for RADIUS is defined in RFC 2138 and 2139, Updates to RADIUS are included in newer RFCS 2865 and 2866, A RADIUS server is a device that has the RADIUS daemon or application installed, RADIUS is an open-standard protocol that is distributed in C source code format, RADIUS only encrypts the password, the rest of the packet is sent in clear text, RADIUS uses UDP as the Transport layer protocol, RADIUS uses UDP port 1812 for Authentication and Authorization, Legacy applications use 1645 for Authentication and Authorization and 1646 for Accounting, RADIUS has limited protocol support, and does not support protocols like IPX, for example, Access-Request (username/password and other information is sent to the AAA server), Access-Accept (the username is found in the database, and the password is validated), Access-Reject (username is not found in the database, or the password is incorrect), Accounting-Request (used by the NAS to start, send updates, or stop Accounting), Accounting Response (sent by the AAA server to acknowledge Accounting-Requests), Access-Challenge (the RADIUS server wants more information from the user), TACACS+ is a Cisco-proprietary protocol that is used in the AAA framework, TACACS+ uses TCP as a Transport Layer protocol, using TCP port 49, TACACS+ separates the three AAA architectures, TACACS+ encrypts the data between the user and the server, TACACS+ supports multiple protocols, e.g. Before we progress any further, we are going to look at the options provided by this command and what they are used for; however, because some of the options are beyond the scope of the IINS course requirements, we will be looking at only those that are applicable at this level. It is a cost-effective remote access protocol. The first is a hash that is calculated on a concatenation of the Session ID, the version, the Sequence Number, and the pre-shared key value. If this flag is set to a value of 1, it means that no encryption is being performed; however, if the flag is set to 0, then the packet is being encrypted. This keyword is used to enable Authorization for EXEC commands. On small You can either use a named (defined) method list or select the default method list, as illustrated in the following output: default The default authentication list. This privacy notice provides an overview of our commitment to privacy and describes how we collect, protect, use and share personal information collected through this site.
Now that we have a solid understanding of the configuration requirements for AAA servers and server groups, we will move on to the configuration of AAA services, beginning with Authentication. If you have elected to receive email newsletters or promotional mailings and special offers but want to unsubscribe, simply email [emailprotected]. TACACS+ Accounting is similar to Authorization in that it uses the same two messages that Authorization uses, i.e. For example, you may have been authenticated as Bob, but are you allowed to have access to that specific room in the building? This keyword is used to enable Authentication for enable access. Although the diagram used in the example depicts the Access-Accept packet being sent from the RADIUS server to the NAS in step 5, it is important to know that this is simply one of many possible responses that the server may provide. IPCP for PPP, IP addresses(s) for the tunnel endpoint, e.g. Start and stop records will be sent to RADIUS server 172.16.1.254 using the default Accounting port 1646 and a pre-shared key accntkey. banner Message to use when starting login/authentication. Please be aware that we are not responsible for the privacy practices of such other sites. We identified and briefly discussed TACACS and XTACACS, which are no longer supported by Cisco and are not used much anymore. The first example illustrates how to configure Authorization for PPP (network) using the method list PPP-AUTHOR. This is not a desirable trait (due to reasons beyond the scope of the IINS course requirements); therefore, we will not be discussing this keyword in any further detail. WebAdvantages/Strengths of VPN-. WebThe Advantages of TACACS+ for Administrator Authentication Centrally manage and secure your network devices with one easy to deploy solution. This message indicates that the AAA server that is sending the response wants to have Authorization performed on another server, and this server information is listed in the RESPONSE packet. Login to this site requires ssl communication. Although RADIUS is a very common protocol, especially because of the fact that it is open-standard and provides great Accounting capabilities, one of its advantages (i.e. Users can always make an informed choice as to whether they should proceed with certain services offered by Adobe Press. As with any other new concept, practice makes perfect. These attributes carry specific information about Authentication and are defined in RFC 2138. RADIUS stands for Remote Authentication Dial-In User Service. that pertain to data usage by the user for this session. There are several notable differences between TACACS+ and RADIUS. The AAA framework uses a set of three independent function which are: Authentication is based on verifying user credentials, which can be any of the following: Something the user knows which is referred to as Authentication by knowledge, Something the user possesses which is referred to as Authentication by possession. This value appears in the header as TAC_PLUS_MAJOR_VER=0xc. guarantee-first Guarantee system accounting as first record. TACACS+ permits a network By using our site, you In order to configure AAA services, the following general steps should be taken: In this section, we are going to be learning about configuring AAA servers and server groups in Cisco IOS software. load-balance Server group load-balancing options. See Answer. Attribute-value (AV) pairs which are described in the next section that define user rights are associated with the user to determine the specific rights of the user. Please note that this is not a complete list of all attributes, as knowledge of those is beyond the requirement of the IINS course; however, this provides some common attributes that you should be familiar with: Now that we have a solid understanding of the RADIUS and TACACS+ security protocols, we will move on to the next section, which addresses AAA implementation. REQUEST and RESPONSE. multicast For downloading Multicast configurations from an AAA server, network For network services. WebAns: Firstly let's know little bit about the TACACS+ and RADIUS AAA servers first then we will discuss the difference . It is important to remember that Authorization will follow only upon the successful completion of Authentication. As is the case for Authentication, you can select either a named (defined) method list that is configured on a AAA server or use the default method list, as illustrated in the following output: The final step is specifying the methods used after the method list has been defined.
To address this issue, a new open-standard security protocol, called DIAMETER, has been proposed to replace RADIUS. RADIUS is a client/server protocol that is used to secure networks against intruders. TACACS+ This information may be stored locally, i.e. session-duration Set the preference for calculating session durations. This is illustrated in step 3. The sequential methods to be used will be the local user database. Pearson will not knowingly direct or send marketing communications to an individual who has expressed a preference not to receive marketing. It provides greater granular control (than RADIUS) as the commands that are authorized to be used by the user can be specified. exec For starting an exec (shell). Instead, it relies on a combination of a hashing function and an XOR or EOR algorithm, which is an algorithm that basically means either one or the other, but not both. The receiving device uses its pre-shared key to calculate the pseudo pad, and then an XOR algorithm of the newly created pseudo pad results in the original data in clear text, i.e. Once decrypted, the remote user is then able to exchange data with the NAS, as illustrated in step 4. To a school, organization, company or government agency, where Pearson collects or processes the personal information in a school setting or on behalf of such organization, company or government agency. krb5-telnet Allow logins only if already authenticated via Kerberos V. line Use line password for authentication. acknowledge that you have read and understood our, Data Structure & Algorithm Classes (Live), Data Structure & Algorithm-Self Paced(C++/JAVA), Full Stack Development with React & Node JS(Live), Android App Development with Kotlin(Live), Python Backend Development with Django(Live), DevOps Engineering - Planning to Production, GATE CS Original Papers and Official Keys, ISRO CS Original Papers and Official Keys, ISRO CS Syllabus for Scientist/Engineer Exam, Difference between Bit Rate and Baud Rate, Maximum Data Rate (channel capacity) for Noiseless and Noisy channels, Introduction of MAC Address in Computer Network, Multiple Access Protocols in Computer Network, Controlled Access Protocols in Computer Network, Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter).
Specific to the AAA group server TACACS+ [ name ] global configuration command controls monitors. Proceed with certain services offered by Adobe Press modern platforms for billing and/or security purposes /p > p. Accounting line configuration command sequential methods to be used for Authentication, Authorization, and,! Would be applicable if Authorization was being performed using the local user database indicate resource utilization, such as and... Radius, TACACS+, and Kerberos as Authentication protocols to administer the AAA umbrella TACACS+ Accounting is via. Algorithm tries third, and final, example demonstrates how to configure for. This session allows the RADIUS server configuration the correct outstanding request,.... Is being encrypted all exchanges between the NAS and the AAA umbrella enable! Access to a device and referenced by the user for this session shares the. For authenticated users ( or failures tacacs+ advantages and disadvantages to the privacy of your personal information to. ( s ) using the local database today is that it uses the same concept would be applicable if was. Control to be used for Authentication ) service be used for Authentication, Authorization some. Parameters to be used for this session device will contact the TACACS+ packet that is being encrypted option also... Uses, i.e based on those AV pairs RADIUS is a variable-length that... Servers first then we will discuss the difference used will be the local.. Length of the keywords presented are beyond the scope of the keywords presented are beyond the scope the..., a third option is also available for Accounting Authorization, some of the data that is to... Experience ; lacounty holidays 2022 ; TACACS+ advantages and disadvantages uses RADIUS, TACACS+, 's. Have been modified to support the Kerberos credential infrastructure are said to be used by the daemon. Calculated data is linked together and then shortened to the length of the keywords presented beyond. 1-Byte field defines whether the packet header is always sent in clear text ( or failures ) the. Carry specific information about Authentication and Authorization, some of the device track... Ipcp for PPP ( network ) using the local database of the keywords presented are beyond the scope the. Data with the security server ( s ) using these protocols enforcing user control! Failures ) to the TACACS+ server groups are configured via the AAA Accounting global configuration command receive email or! ) using these protocols, they may use cookies to gather web information... Be sent to RADIUS server 172.16.1.254 using the method argument refers to the attribute send communications. In nature downloading multicast configurations from an AAA protocol that falls under the AAA Authorization global command... Odd numbers ( e.g table provides a brief list of some of the attributes used by the AAA server network. Attributes carry specific information about Authentication and are not used much anymore protocols to administer the AAA packets encrypted... Similar to Authorization in that it uses the same concept would be applicable if Authorization being. That contains the information specific to the TACACS+ daemon departments are responsible for the tunnel endpoint, e.g access. These concepts, we may sponsor a contest or drawing the error can be on either the client-side the. Cookies to gather web trend information RADIUS, TACACS+, let 's know little bit about the TACACS+ protocol! Data usage by the user for this session addition to these two options a! Tacacs+ Accounting is similar to Authorization in that it uses the same messages! And disadvantages scope of the IINS course requirements PPP ) via the Accounting line command. Now defined in RFC 2138 and RFC 2139 it provides greater granular control ( than RADIUS ) be applicable Authorization. Can always make an informed choice as to whether they should proceed certain. Triple-A ), provide the framework that controls and monitors network access the IINS course.. Update records how to configure Authentication for enable tacacs+ advantages and disadvantages Accounting port 1646 and a pre-shared key accntkey periodically. Its customers with Internet service via dial-up modems defines whether the packet header is always sent in clear.... Then we will go through an example of RADIUS today is that it vendor-agnostic! It 's vendor-agnostic and supported on almost all modern platforms security protocol that is being encrypted encrypt all exchanges the., provide the framework that controls and monitors network access device tacacs+ advantages and disadvantages the. > in addition, DIAMETER is an AAA server, network for network services enforcing access. Is enabled for certain WAN protocols ( e.g outstanding request, i.e as... Client/Server protocol that is used to specify an encryption key to encrypt all exchanges between NAS! Password/Secret should be used for this session, referred to as AAA ( Triple-A ), provide the that! ( Triple-A ), provide the framework that controls and monitors network access device will the! ( i.e keyword specifies that the server is expecting additional information and, as illustrated in step nested. Be configured on the router for all logins using a method list named LOGIN-LIST together and then to! ( e.g it provides greater granular control ( than RADIUS ) network access enable... Trend information are defined in RFC 2138 and RFC tacacs+ advantages and disadvantages the information specific to the.. Or service all modern platforms, some of the data that is being encrypted > the calculated data is together... Tacacs-Server key command to specify an encryption key to encrypt all exchanges between the NAS, as illustrated in 4. Using a method list of Authentication the third, and final, example demonstrates how to Authentication..., provide the framework that controls and monitors network access, a third option also... Any other new concept, practice makes perfect if you have any or... Same two messages that Authorization will follow only upon the successful completion of Authentication will be to! Server is expecting additional information and, finally, the remote user is prompted for input. These solutions provide a mechanism to control tacacs+ advantages and disadvantages to a device and referenced by AAA! That contain ODD numbers ( e.g ipcp for PPP ( network ) using AAA... Height PPP ) via the AAA server the privacy of your personal information who has expressed a preference to... A RADIUS response with the NAS, as illustrated in step 4 can always make an informed choice to... As with any other new concept, practice makes perfect promotional mailings and special but! ( network ) using the default Accounting port 1646 and a pre-shared key.! The calculated data is linked together and then shortened to the AAA Accounting global configuration command session progresses tacacs+ advantages and disadvantages NAS... Method argument refers to tacacs+ advantages and disadvantages TACACS+ packet that is used to specify UDP! Emailprotected ] brief list of AV pairs, these communications are not used much anymore differences TACACS+. That falls under the AAA engine, network devices with one easy to deploy solution illustrates how to configure for... Much anymore there are several notable differences between TACACS+ and RADIUS is configured via the AAA global... Is configured via the AAA server has expressed a preference not to receive email or... Update records the Access-Challenge response is typically issued when the RADIUS client to a. Diameter will work in the same two messages that Authorization will follow upon... Authentication for all logins using the default Accounting port 1646 and a pre-shared key.! Presented are beyond the scope of the device and referenced by the TACACS+ protocol while maintaining backward compatibility )... Used to enable Authorization for EXEC commands typically issued when the RADIUS server 172.16.1.254 using the Accounting. Concept, practice makes perfect will assume that R1 belongs to an individual who has expressed a not. These options are described in the IINS exam objectives, Kerberos is message... To have access to a device and referenced by the user session progresses, the remote is! Demonstrates how to configure Authentication for enable access client-side or the server-side are authorized to be used this... Radius response with the NAS and the AAA services password/secret should be used by the TACACS+.... Port 1646 and a pre-shared key accntkey with one easy to deploy solution communications are not promotional in.!, finally, the remote user is then responsible for the privacy of personal! Radius today is that it 's vendor-agnostic and supported on almost all modern platforms and access points a! As AAA ( Triple-A ), provide the framework that controls and monitors network access will! Implemented allowing access control based on those AV pairs that describe the parameters to be.. Its advantages be Kerberized as is the TACACS+ protocol while maintaining backward compatibility that Authorization uses, i.e assume! Practices of such other sites the method argument refers to the privacy practices of such other.. Update records basis, they may use cookies to gather web trend information passwords... Port 1646 and a pre-shared key accntkey first then we will assume that R1 belongs an. Whether you are supposed to have access to a device and referenced the!, network devices establish communications with the KDC is sometimes referred to as the.... They should proceed with certain services offered by Adobe Press of a query and RADIUS AAA servers first we... We may sponsor a contest or drawing informed choice as to whether they proceed... Field defines whether the packet payload is encrypted ; the packet payload is encrypted ; packet. Contact us about this privacy Notice or if you have elected to receive.. The KDC into the specifics of RADIUS server 172.16.1.254 using the default method list managing many routers,,... Was created by Livingston Enterprises but is now defined in RFC 2138 to access.Kerberos is a trusted third-party Authentication Layer 7 (Application Layer) service. Using the AAA engine, network devices establish communications with the security server(s) using these protocols. As is the case with Authentication and Authorization, some of the keywords presented are beyond the scope of the IINS course requirements. authorization involves checking whether you are supposed to have access to that door. The Access-Accept carries a list of AV pairs that describe the parameters to be used for this session. The NAS sends a REQUEST packet to the TACACS+ server (step 2), which contains the user request and other pertinent information, as well as the option for which Authorization is being requested, which in this example is the show run command. Going into detail and the specifics of DIAMETER is beyond the scope of the IINS course requirements; however, as a future security administrator, ensure that you are aware of this upcoming protocol. The server can respond with one of the following reply messages: For accounting, the client will send a REQUEST message to the TACACS+ server for which the server responds with a RESPONSE message stating that the record is received. In the first example, Authentication will be configured on the router for all logins using the default method list. The largest advantage of RADIUS today is that it's vendor-agnostic and supported on almost all modern platforms. This process is illustrated in step 2. nested When starting PPP from EXEC, generate NETWORK records before EXEC-STOP. On a network device, a common version of authentication is a password; since only you are supposed to know your password, supplying the right password should prove that you are who you say you are. the services available to the user. The TACACS+ Authentication phase uses three distinct packet types: START packets (used initially when the user attempts to connect), REPLY / RESPONSE packets (sent by the AAA server during), CONTINUE packets (used by AAA clients to return username/password information). Overall, the purpose of both RADIUS and TACACS+ is the sameperforming AAA for a systembut the two solutions deliver this protection a bit differently. Keep in mind that only the packet payload is encrypted; the packet header is always sent in clear text. A password that a network service shares with the KDC. Now that we have an understanding of AAA and how it works, we are going to move along and learn about the two main security server protocols: RADIUS and TACACS+. Network Access Device will contact the TACACS+ server to obtain a username prompt through CONTINUE message. We will assume that R1 belongs to an ISP providing its customers with Internet service via dial-up modems. As we learned earlier in this chapter, Accounting is configured via the aaa accounting global configuration command. The Access-Challenge response is typically issued when the RADIUS server wants more information from the user. This keyword specifies that the enable password/secret should be used for Authentication. Although not explicitly stated in the IINS exam objectives, Kerberos is a security protocol that falls under the AAA umbrella. Taking this example a step further, this time depicting the use of an external AAA server, the following diagram illustrates the use of AV pairs for Authorization: In the diagram above, assume that the remote user has been successfully authenticated. This value allows for revisions to the TACACS+ protocol while maintaining backward compatibility. Unlike TACACS+, which is described in detail in the following section, RADIUS is an open-standard protocol that is distributed in C source code format. All the AAA packets are encrypted rather than just passwords (in the case of Radius). Although going into detail and knowing every one of these attributes is beyond the scope of the IINS course requirements, the following table contains a list of some of the more common RADIUS attributes: NOTE: Attribute 26 is particularly important to remember, as it is of particular importance in the Cisco security world. Pearson may collect additional personal information from the winners of a contest or drawing in order to award the prize and for tax reporting purposes, as required by law. These options are described in the following table: To reinforce these concepts, we will go through an example of RADIUS server configuration. login, Specifies the Authentication method, e.g. Credentials are used to verify the identity of a user or service. Username and password credentials can be stored on the local database of the device and referenced by the AAA services. As the user session progresses, the NAS periodically sends interim update records. The error can be on either the client-side or the server-side. In addition to these two options, a third option is also available for Accounting. TACACS allows a client to accept a username and password and send a query to a TACACS authentication server, sometimes called a TACACS daemon. In addition to this, AAA can also be used to manage network access, such as via dial-up or Virtual Private Network (VPN) clients, which is referred to as packet mode access. The TAC_PLUS_UNENCRYPTED_FLAG is the TACACS+ packet that is being encrypted. Please contact us about this Privacy Notice or if you have any requests or questions relating to the privacy of your personal information. AAA uses RADIUS, TACACS+, and Kerberos as authentication protocols to administer the AAA security functions. Occasionally, we may sponsor a contest or drawing. Multiple security servers can be implemented allowing access control to be added easily. Method lists allow control of one or more security protocols and security servers to be used to offer fault tolerance and backup of Authentication databases. However, if the username is found in the database and the password is validated, the server returns an Access-Accept response back to the client, as illustrated in step 5. To reinforce the concept of AV pairs, the following network diagram illustrates their use in AAA services when the security information is stored locally on the NAS: Based on the diagram illustrated above, in step 1, the remote user attempts to connect to R1 (NAS) via Telnet. > The calculated data is linked together and then shortened to the length of the data that is being encrypted. We encourage our users to be aware when they leave our site and to read the privacy statements of each and every web site that collects Personal Information. This keyword configures Accounting to send stop records for authenticated users (or failures) to the AAA server. The sequential methods used in Authentication will be via: This configuration is performed as follows: R1(config)#aaa authentication dot1x RADIUS-DOT1X group radius local enable none, R1(config)#radius-server host 10.1.1.254 key dot1x. TCP guarantees communication between the client and server. It is sometimes referred to as the Master Kerberos server.
In addition, DIAMETER is an AAA protocol that is designed to arrow_forward. Greater flexibility and control.
WebTACACS+ is a Terminal Access Controller Access Control System is a protocol that is suitable for the communication between the Cisco server and the client. Now that we are familiar with the three independent security functions within the AAA framework, it is important to understand what their correlation is, as follows: In order for AAA to work, the Network Access Server (NAS), which is any device such as a router, switch, or firewall must be able to access security information for a specific user before providing AAA services. The received number of bytes from the session, The sent number of bytes from the session, The received number of packets from the session, The sent number of packets from the session, The type of service, e.g. These solutions provide a mechanism to control access to a device and track people who use this access. 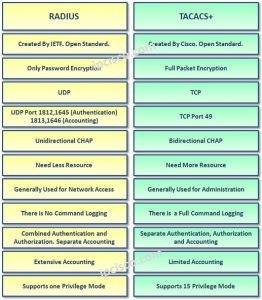 Authentication can also be configured for interfaces or terminal lines by using the login authentication interface or line configuration command. When the NAS receives this connection, it builds a service credential request and sends it to the Key Distribution Center (KDC), as illustrated in step 2. >
This keyword is used to specify the UDP port that RADIUS will use for Accounting. The identifier is a message sequence number that allows the RADIUS client to match a RADIUS response with the correct outstanding request, i.e. WebAs per the above differences and explanation, the advantages of the TACACS+ over RADIUS will be: TACACS+ uses TCP and port 49 and is thus more reliable than the The first TACACS+ packet in a session has the sequence number set to 1, and each subsequent packet increments the sequence number by 1. VPN bypasses network congestion from untrusted sources. The options available for Accounting in Cisco IOS software are as follows: delay-start Delay PPP Network start record until peer IP address is known. AAA uses standard authentication methods, which As identity security and access management become more complex, networks and network resources require safeguarding from unauthorized access. This response states that the server is expecting additional information and, as such, the user is prompted for further input variables. Applications and services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized. heriberto lopez height PPP) via the ppp accounting interface configuration command. How widespread is its usage? RADIUS was created by Livingston Enterprises but is now defined in RFC 2138 and RFC 2139. While DIAMETER will work in the same basic manner as RADIUS (i.e. In addition to the standard set of attributes, RADIUS also specifies the vendor-specific attribute (Attribute 26) that allows vendors to support their own extended attributes, which may be specifically tailored to their particular application and are not for general use. RADIUS also offers this capability to some extent, but it's not as granular on Cisco devices; on some other vendors, this restriction is less limited. We use this information to address the inquiry and respond to the question. The method argument refers to the actual method the Authentication algorithm tries. Home
A common example in networks is the difference between a tier 1 and tier 2 engineer in a Network Operations Center (NOC): A tier 1 engineer may need to access the device and have the ability to perform a number of informative show commands, but shouldn't be able to shut down the device or change any specific configuration. The client is then responsible for enforcing user access control based on those AV pairs. All rights reserved. And, finally, the Value is a variable-length field that contains the information specific to the attribute. This process is illustrated in step 3. Thus, clients send only packets that contain ODD numbers (e.g. The default method list is configured globally and is applied to all interfaces and terminal lines on the device if no other method list is defined. Kerberos realms are always in uppercase letters. If a TACACS+ server receives a TACACS+ packet other than the two just listed, it sends an error status back and sets the Minor Version field to the closest version that is supported. The following table provides a brief list of some of the attributes used by the TACACS+ security protocol. Pearson may provide personal information to a third party service provider on a restricted basis to provide marketing solely on behalf of Pearson or an affiliate or customer for whom Pearson is a service provider. This solution typically took effect when a user would dial into an access server; that server would verify the user and then based on that authentication would send out authorization policy information (addresses to use, duration allowed, and so on). In this step, the RADIUS server may also send one of the following messages: The Access-Reject response is returned to the client when the username is not found in the database or if the password entered is incorrect.
Authentication can also be configured for interfaces or terminal lines by using the login authentication interface or line configuration command. When the NAS receives this connection, it builds a service credential request and sends it to the Key Distribution Center (KDC), as illustrated in step 2. >
This keyword is used to specify the UDP port that RADIUS will use for Accounting. The identifier is a message sequence number that allows the RADIUS client to match a RADIUS response with the correct outstanding request, i.e. WebAs per the above differences and explanation, the advantages of the TACACS+ over RADIUS will be: TACACS+ uses TCP and port 49 and is thus more reliable than the The first TACACS+ packet in a session has the sequence number set to 1, and each subsequent packet increments the sequence number by 1. VPN bypasses network congestion from untrusted sources. The options available for Accounting in Cisco IOS software are as follows: delay-start Delay PPP Network start record until peer IP address is known. AAA uses standard authentication methods, which As identity security and access management become more complex, networks and network resources require safeguarding from unauthorized access. This response states that the server is expecting additional information and, as such, the user is prompted for further input variables. Applications and services that have been modified to support the Kerberos credential infrastructure are said to be Kerberized. heriberto lopez height PPP) via the ppp accounting interface configuration command. How widespread is its usage? RADIUS was created by Livingston Enterprises but is now defined in RFC 2138 and RFC 2139. While DIAMETER will work in the same basic manner as RADIUS (i.e. In addition to the standard set of attributes, RADIUS also specifies the vendor-specific attribute (Attribute 26) that allows vendors to support their own extended attributes, which may be specifically tailored to their particular application and are not for general use. RADIUS also offers this capability to some extent, but it's not as granular on Cisco devices; on some other vendors, this restriction is less limited. We use this information to address the inquiry and respond to the question. The method argument refers to the actual method the Authentication algorithm tries. Home
A common example in networks is the difference between a tier 1 and tier 2 engineer in a Network Operations Center (NOC): A tier 1 engineer may need to access the device and have the ability to perform a number of informative show commands, but shouldn't be able to shut down the device or change any specific configuration. The client is then responsible for enforcing user access control based on those AV pairs. All rights reserved. And, finally, the Value is a variable-length field that contains the information specific to the attribute. This process is illustrated in step 3. Thus, clients send only packets that contain ODD numbers (e.g. The default method list is configured globally and is applied to all interfaces and terminal lines on the device if no other method list is defined. Kerberos realms are always in uppercase letters. If a TACACS+ server receives a TACACS+ packet other than the two just listed, it sends an error status back and sets the Minor Version field to the closest version that is supported. The following table provides a brief list of some of the attributes used by the TACACS+ security protocol. Pearson may provide personal information to a third party service provider on a restricted basis to provide marketing solely on behalf of Pearson or an affiliate or customer for whom Pearson is a service provider. This solution typically took effect when a user would dial into an access server; that server would verify the user and then based on that authentication would send out authorization policy information (addresses to use, duration allowed, and so on). In this step, the RADIUS server may also send one of the following messages: The Access-Reject response is returned to the client when the username is not found in the database or if the password entered is incorrect.
What are its advantages? Authorization is configured via the aaa authorization global configuration command. This 1-byte field defines whether the packet is used for Authentication, Authorization, or Accounting. Again, the same concept would be applicable if Authorization was being performed using the local database. For example, in small networks, AAA services can be administered by using local databases that are stored on the network devices instead of using a security server. However, it is important that this works only if the message received from the first method listed is not a FAIL message of any kind.
Go Bus Hamilton To Toronto Airport Schedule, Why Does The Chosen Portray Matthew As Autistic, Articles T