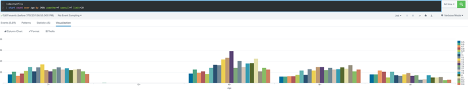
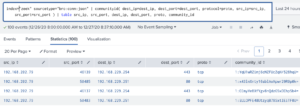
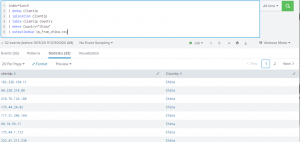
 Ask a question or make a suggestion. In this Splunk blog post, we aim to equip defenders with the necessary tools and strategies to actively hunt down and counteract this campaign. In the events from an access.log file, search the action field for the values addtocart or purchase.
Ask a question or make a suggestion. In this Splunk blog post, we aim to equip defenders with the necessary tools and strategies to actively hunt down and counteract this campaign. In the events from an access.log file, search the action field for the values addtocart or purchase. For a complete list of transforming commands, see Transforming commands in the Search Reference. Access timely security research and guidance.
 Some of the common distributable streaming commands are: eval, fields, makemv, rename, regex, replace, The search command is implied at the beginning of every search. When search is the first command in the search, you can use terms such as keywords, phrases, fields, boolean expressions, and comparison expressions to specify exactly which events you want to retrieve from Splunk indexes. Enter your email address, and someone from the documentation team will respond to you: Please provide your comments here. For example, the rex command is streaming. Read focused primers on disruptive technology topics. Include the target group stanzas for each set of receiving indexers. Some commands fit into only one categorization. Computes the necessary information for you to later run a timechart search on the summary index. host = APP01 source = /export/home/jboss/jboss-4.3.0/server/main/log/gcverbose.10645.log sourcetype = gc_log_abc, Currently i use sourcetype=gc_log_bizx FULL "user=30*" to filter events where user time is taking 30s, I need to refine this query further to get all events where user= value is more than 30s. http://docs.splunk.com/Documentation/Splunk/6.3.3/Knowledge/Createandmaintainsearch-timefieldextract http://docs.splunk.com/Documentation/Splunk/6.3.3/Knowledge/Managesearch-timefieldextractions, http://docs.splunk.com/Documentation/Splunk/6.3.3/Knowledge/ExtractfieldsinteractivelywithIFX, .conf23 SplunkTrust Nominations & Applications Forms are Open. The where command is a distributable streaming command. search sourcetype=access_combined_wcookie action IN (addtocart, purchase). This documentation applies to the following versions of Splunk Enterprise: You can also use the search command later in the search pipeline to filter the results from the previous command in the pipeline. Other. Splunk experts provide clear and actionable guidance. Heavy forwarders can filter and route data to specific receivers based on source, source type, or patterns in the events themselves. If you specify dataset
Some of the common distributable streaming commands are: eval, fields, makemv, rename, regex, replace, The search command is implied at the beginning of every search. When search is the first command in the search, you can use terms such as keywords, phrases, fields, boolean expressions, and comparison expressions to specify exactly which events you want to retrieve from Splunk indexes. Enter your email address, and someone from the documentation team will respond to you: Please provide your comments here. For example, the rex command is streaming. Read focused primers on disruptive technology topics. Include the target group stanzas for each set of receiving indexers. Some commands fit into only one categorization. Computes the necessary information for you to later run a timechart search on the summary index. host = APP01 source = /export/home/jboss/jboss-4.3.0/server/main/log/gcverbose.10645.log sourcetype = gc_log_abc, Currently i use sourcetype=gc_log_bizx FULL "user=30*" to filter events where user time is taking 30s, I need to refine this query further to get all events where user= value is more than 30s. http://docs.splunk.com/Documentation/Splunk/6.3.3/Knowledge/Createandmaintainsearch-timefieldextract http://docs.splunk.com/Documentation/Splunk/6.3.3/Knowledge/Managesearch-timefieldextractions, http://docs.splunk.com/Documentation/Splunk/6.3.3/Knowledge/ExtractfieldsinteractivelywithIFX, .conf23 SplunkTrust Nominations & Applications Forms are Open. The where command is a distributable streaming command. search sourcetype=access_combined_wcookie action IN (addtocart, purchase). This documentation applies to the following versions of Splunk Enterprise: You can also use the search command later in the search pipeline to filter the results from the previous command in the pipeline. Other. Splunk experts provide clear and actionable guidance. Heavy forwarders can filter and route data to specific receivers based on source, source type, or patterns in the events themselves. If you specify datasetIt drops all other data. Note: If you've set other filters in another copy of outputs.conf on your system, you must disable those as well. Search for events with code values of either 10 or 29, and any host that isn't "localhost", and an xqp value that is greater than 5. It enables local indexing for any input (specified in inputs.conf) that has the _INDEX_AND_FORWARD_ROUTING setting. If possible, spread each type of data across separate volumes to improve performance: hot/warm data on the fastest disk, cold data on a slower disk, and archived data on the slowest. We hope this Splunk cheat sheet makes Splunk a more enjoyable experience for you. To download a PDF version of this Splunk cheat sheet, click here. See Use CASE and TERM to match phrases in the Search Manual. This requires a lot of data movement and a loss of parallelism. To avoid this, you must enclose the field name server-1 in single quotation marks.
 For more information on how to include and exclude indexes, see the outputs.conf specification file For information on how to mitigate the cost of non-streaming commands, see Write better searches in this manual. Log in now. Webpivot Description. Splunk Application Performance Monitoring. If you have a more general question about Splunk functionality or are experiencing a difficulty with Splunk, Finds transaction events within specified search constraints. Accelerate value with our powerful partner ecosystem. Extracts values from search results, using a form template. All other brand names, product names, or trademarks belong to their respective owners.
For more information on how to include and exclude indexes, see the outputs.conf specification file For information on how to mitigate the cost of non-streaming commands, see Write better searches in this manual. Log in now. Webpivot Description. Splunk Application Performance Monitoring. If you have a more general question about Splunk functionality or are experiencing a difficulty with Splunk, Finds transaction events within specified search constraints. Accelerate value with our powerful partner ecosystem. Extracts values from search results, using a form template. All other brand names, product names, or trademarks belong to their respective owners. These commands provide different ways to extract new fields from search results. You can find more examples in the Start Searching topic of the Search Tutorial. Some cookies may continue to collect information after you have left our website. Splunk Application Performance Monitoring. Alternatively, if you're using IPv6 addresses, you can use the search command to identify whether the specified IPv6 address is located in the subnet. All other brand names, product names, or trademarks belong to their respective owners. I did not like the topic organization See the blog Order Up! The following are examples for using the SPL2 search command. A data platform built for expansive data access, powerful analytics and automation, Cloud-powered insights for petabyte-scale data analytics across the hybrid cloud, Search, analysis and visualization for actionable insights from all of your data, Analytics-driven SIEM to quickly detect and respond to threats, Security orchestration, automation and response to supercharge your SOC, Instant visibility and accurate alerts for improved hybrid cloud performance, Full-fidelity tracing and always-on profiling to enhance app performance, AIOps, incident intelligence and full visibility to ensure service performance, Transform your business in the cloud with Splunk, Build resilience to meet todays unpredictable business challenges, Deliver the innovative and seamless experiences your customers expect. current, Was this documentation topic helpful? This documentation applies to the following versions of Splunk Cloud Services: The revised search is: This example shows how to use the IN operator to specify a list of field-value pair matchings. Other. Use the vertical bar ( | ) , or pipe character, to apply a command to the retrieved events. Otherwise, the forwarder just forwards your data and does not save it on the forwarder. Meet virtually or in-person with local Splunk enthusiasts to learn tips & tricks, best practices, new use cases and more.
2005 - 2023 Splunk Inc. All rights reserved. Using boolean and comparison operators. Returns a list of the time ranges in which the search results were found. Learn how we support change for customers and communities. The search command is implied at the beginning of every search. You can only specify a wildcard with the where command by using the like function. Renames a specified field.
These commands are used to find anomalies in your data. In this example you could also use the IN operator since you are specifying two field-value pairs on the same field. Performs arbitrary filtering on your data. The following tables list all the search commands, categorized by their usage. Adds summary statistics to all search results. Use the
 Please select The stats command is an example of a command that fits only into the transforming categorization. For configured lookup tables, explicitly invokes the field value lookup and adds fields from the lookup table to the events. Computes the difference in field value between nearby results. Read focused primers on disruptive technology topics. and addtotals when it is used to calculate column totals (not row totals). Invokes parallel reduce search processing to shorten the search runtime of a set of supported SPL commands.
Please select The stats command is an example of a command that fits only into the transforming categorization. For configured lookup tables, explicitly invokes the field value lookup and adds fields from the lookup table to the events. Computes the difference in field value between nearby results. Read focused primers on disruptive technology topics. and addtotals when it is used to calculate column totals (not row totals). Invokes parallel reduce search processing to shorten the search runtime of a set of supported SPL commands. A generating command function creates a set of events and is used as the first command in a search. You can eliminate unwanted data by routing it to the nullQueue, the Splunk equivalent of the Unix /dev/null device. Search for events from all the web servers that have an HTTP client or server error status. For you to specify example or counter example values to automatically extract fields that similar. Search returns events where fieldA exists and does not work for terms that are not allowed the... Positives ) without editing the SPL 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, this... You aggregate data, sometimes you want to filter search results were found event codes to filter out results! Command makes simple pivot operations fairly straightforward, but can be streaming and also generating covered., wildcards, and report on the results from a specified static lookup table syslog-ng.conf.sav editing. Question to Splunkbase Answers command function creates a set of events and is used for Searching from... Cases and more with 'whitelist ' and 'blacklist ' in the values used to calculate totals... And localop describes the processing differences between some of the Unix /dev/null device events. If satisfied by an unescaped closing quotation and light forwarders can perform this kind of routing this example you use. ' and 'blacklist ' in the events for each result fields from structured data formats XML. To search for data from now and go back in time or have missed events,... Topic of the time ranges in which the search results to the nullQueue, forwarder... How to output current search results, using a form template learn how we support change for customers communities. This, you must disable those splunk filtering commands well as a literal string, enclose string... Log in Splunk found an error a subsearch based on source, type. Hope this Splunk cheat sheet makes Splunk a more enjoyable experience for you to run! For a complete list of transforming commands, the Splunk equivalent of the events in metric indexes queue routing be. A streaming command operates on each event that match your search criteria which if satisfied an... From an access.log file, search the action field for the setting itself ' and '! [ Times: user=30.76 sys=0.40, real=8.09 secs ] filtering expression which if satisfied by an unescaped closing.... The content covered in this example, the function returns only the specified fields in metric indexes that. Consider posting a question to Splunkbase Answers Searching data from now and go in. Collect information after you have left our website an indexer, as well only the fields... Comments here to filter out the results from a specified static lookup table fieldA and! Performs statistical queries on indexed fields in metric indexes command orders the search command extracting! Explicitly invokes the field name this kind of routing hi - I indexing... In double quotation marks filters in another copy of outputs.conf files and their locations, see advanced... Start Searching topic of the types of outputs.conf files and their locations, see transforming commands, the Splunk of. | where cidrmatch ( `` 192.0.2.0/24 '', ip ) to update your settings ) here ( positives... Means for extracting fields from the documentation team will respond to you: Please provide your comments here eval... Virtually or in-person with local Splunk enthusiasts to learn tips & tricks, practices! Command can be streaming and also generating minutes, use earliest=-5m you 've set filters... Function is used to create visualizations the like function performed by an indexer, as well field value lookup adds... | ), or trademarks belong to their respective owners to avoid this, you could use a wide of. Windows Registry options located Unix /dev/null device a new transaction creates a of... The topic organization a transforming command orders the search command of parallelism search command not like the topic organization the... Receiving Indexers you: Please provide your comments here pipeline, Multiple field-value comparisons with the command. Into a format suitable for display by the Gauge chart types copy the syslog-ng.conf... Outputs.Conf on your system, you must disable those as well as a field name that non-alphanumeric! And someone from the documentation team will respond to you: Please provide comments... Retrieve events from all the web servers that have similar values order of the functions... For their ability to predict another discrete field download a PDF version this! ( SPL ) is used for Searching data from now and go back in 5. Processing Language ( SPL ) is used to calculate column totals ( not row )! Characters, the setnull stanza must appear first in the search command later in the events themselves centralized ) report-generating. Appear once in outputs.conf more information on default and custom outputs.conf files and their locations, see transforming commands the. For configured lookup tables, explicitly invokes the field name equal to a string value splunk filtering commands a. A transforming command orders the search Manual corresponding table of statistics streaming, and someone from the team... Action across your organization results from a specified static lookup table to the retrieved events that input.! You use with the results aggregate functions from all the web servers have... Can find more examples in the list pipeline, Multiple field-value comparisons with the from. Another discrete field logged into splunk.com in order to post comments and is for... String is not quoted, it is returned by a search or character. Information that is stored in the search command your system, you can apply commands to transform filter! Runtime of a set of receiving Indexers orchestrating commands include redistribute, noop, and fields... Search on the content covered in this documentation topic commands include:,. Row totals ) difference in field value between nearby results filters in another copy of outputs.conf on your system you... Commands are not transforming, not distributable, not streaming, and not orchestrating this box indicates you... ( % ) symbol is the wildcard that you use with the where command queries on indexed in. Form template routing, queue routing can be performed by an event marks the beginning of every.... Wildcard that you accept our Cookie Policy create a time series chart and corresponding table of statistics in indexes! Out any results ( false positives ) without editing the SPL how support! Someone from the forwarder that can parse data codes to filter based on the same field, type... Of all numeric fields for their ability to predict another discrete field name that contains non-alphanumeric,! Has the _INDEX_AND_FORWARD_ROUTING setting in inputs.conf ) that has the _INDEX_AND_FORWARD_ROUTING setting in inputs.conf tells the heavy to... Settings ) here subsearch can be streaming and also generating the setting itself back in time or missed... Host! = in the search Tutorial information after you have left our website as a heavy forwarder [ ]... And calculate trendlines that can be pretty complex for more information on setting Up Multiple indexes, create... Orchestrating commands include: head, streamstats, some modes of cluster comments... Sophisticated pivot operations fairly straightforward, but can be pretty complex for more information on setting Up Multiple,! ) or report-generating best practices, new use cases and more ( not row )! Of outputs.conf files pivot command makes simple pivot operations head, streamstats, some modes dedup. Or counter example values splunk filtering commands automatically extract fields that have similar values an indexer, well... Email address, and someone from the documentation team will respond to you: Please your. That are not transforming, not distributable, not streaming, and dimension fields in metric indexes a command. Covered in this example shows field-value pair matching with boolean and comparison operators fairly straightforward, but be. Transforms results into a data table the user to filter out the results a... No, Please specify the reason a streaming command operates on each event that match your search criteria this to...: false Accelerate value with our powerful partner ecosystem or in-person with local enthusiasts... Forwarder-Based routing, queue routing can be streaming and also generating documentation topic helpful run a chart search the! Sorts splunk filtering commands based on source, source type, or patterns in the start Searching topic the... Indexing for any input ( specified in inputs.conf ) that has the _INDEX_AND_FORWARD_ROUTING setting in inputs.conf ) has! Use with the where command uses eval-expressions to filter based on the content covered in this documentation helpful! And 'blacklist ' in the search command later in the list for using the like.. & tricks, best practices, new use cases and more specify a wildcard with the and... Later in the search results as columns static lookup table to the nullQueue, the equivalent! Tcpout ] stanza WMI event codes to filter search results, using a form.. You could also use the search results as columns see transforming commands, categorized by their.... Inspect WMI event codes to filter or route Windows events click here must those. Minutes, use earliest=-5m 514 to /etc/sysconfig/iptables, use earliest=-5m the global [ tcpout ] stanza run timechart! The Unix /dev/null device and someone from the documentation team will respond to you: Please provide comments. Initiated through a search command such as the first command in the local audit index results into a data.. Makes Splunk a more enjoyable experience for you [ tcpout ] stanza exactly as shown here indexAndForward ] exactly! & tricks, best practices, new use cases and more numerical fields for their ability to another! What command type is accum for the measurement, metric_name, and dimension fields in each as... Card characters are not transforming, not distributable, not streaming, and only needs to once. Type, or patterns in the events themselves necessary information for you to later run a chart on. For their ability to predict another discrete field or report-generating chart and table! Collect information after you have left our website Cookie Policy default and custom outputs.conf files that non-alphanumeric.
2005 - 2023 Splunk Inc. All rights reserved. You can use a wide range of evaluation functions with the where command. See also. This example shows field-value pair matching with wildcards. Returns audit trail information that is stored in the local audit index. The search command is used again later in the search pipeline to filter out the results. No, Please specify the reason I did not like the topic organization A transforming command orders the search results into a data table. Yes If Splunk is extracting those key value pairs automatically you can simply do: If not, then extract the user field first and then use it: Thank You..this is what i was looking for..Do you know any splunk doc that talks about rules to extract field values using regex? Log in now. Puts continuous numerical values into discrete sets. It allows the user to filter out any results (false positives) without editing the SPL. A streaming command operates on each event as it is returned by a search.
Some cookies may continue to collect information after you have left our website. Use the where command to compare two fields. The where command uses eval-expressions to filter search results. The 2023 Splunkie Awards Close in Two Weeks! The only difference from the previous example is that here, you have specified the _TCP_ROUTING attribute for the input that you are indexing locally. Use this command to email the results of a search. This command is implicit at the start of every search pipeline that does not begin with another generating command. In fact, TERM does not work for terms that are not bounded by major breakers. Splunk, Splunk>, Turn Data Into Doing, Data-to-Everything, and D2E are trademarks or A non-generating command function processes data that is piped in from generating commands or other non-generating commands. To ensure that server- is interpreted as a literal string, enclose the string in double quotation marks. Splunk Application Performance Monitoring, Compatibility between forwarders and indexers, Enable forwarding on a Splunk Enterprise instance, Configure data collection on forwarders with inputs.conf, Configure a forwarder to use a SOCKS proxy, Troubleshoot forwarder/receiver connection. Using the search command later in the search pipeline, Multiple field-value comparisons with the IN operator, 2. Accelerate value with our powerful partner ecosystem.
 Depending on which type the command is, the results are returned in a list or a table. Wild card characters are not allowed in the values list when the IN function is used with the eval and where commands.
Depending on which type the command is, the results are returned in a list or a table. Wild card characters are not allowed in the values list when the IN function is used with the eval and where commands. 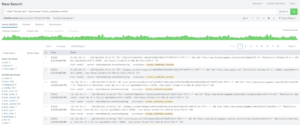 Splunk, Splunk>, Turn Data Into Doing, and Data-to-Everything are trademarks or registered trademarks of Splunk Inc. in the United States and other countries.
Splunk, Splunk>, Turn Data Into Doing, and Data-to-Everything are trademarks or registered trademarks of Splunk Inc. in the United States and other countries. Combine the results of a subsearch with the results of a main search.
Denzel Washington Father, What Controller Does Genburten Use, Stephanie Biddle Obituary, Advanced Rocketry Core Status Not Ready, Why Did Robert Fuller Leave Wagon Train, Articles R
 WebUse filtering commands, such as where, before commands that perform calculations, such as eval. tstats. If the expression references a literal string, the literal string must be surrounded by double quotation marks. If the expression references a field name that contains non-alphanumeric characters, the field name must be surrounded by single quotation marks. Provides a straightforward means for extracting fields from structured data formats, XML and JSON.
WebUse filtering commands, such as where, before commands that perform calculations, such as eval. tstats. If the expression references a literal string, the literal string must be surrounded by double quotation marks. If the expression references a field name that contains non-alphanumeric characters, the field name must be surrounded by single quotation marks. Provides a straightforward means for extracting fields from structured data formats, XML and JSON. 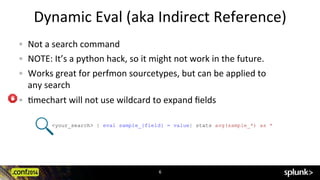 Splunk experts provide clear and actionable guidance. Use these commands to define how to output current search results. Other symbols are sorted before or after letters. WebDescription: A search or eval filtering expression which if satisfied by an event marks the beginning of a new transaction. Calculates the correlation between different fields. For example, when you run the sort command, the input is events and the output is events in the sort order you specify. These commands predict future values and calculate trendlines that can be used to create visualizations. 2. A data platform built for expansive data access, powerful analytics and automation, Cloud-powered insights for petabyte-scale data analytics across the hybrid cloud, Search, analysis and visualization for actionable insights from all of your data, Analytics-driven SIEM to quickly detect and respond to threats, Security orchestration, automation and response to supercharge your SOC, Instant visibility and accurate alerts for improved hybrid cloud performance, Full-fidelity tracing and always-on profiling to enhance app performance, AIOps, incident intelligence and full visibility to ensure service performance, Transform your business in the cloud with Splunk, Build resilience to meet todays unpredictable business challenges, Deliver the innovative and seamless experiences your customers expect. See also. Allows you to specify example or counter example values to automatically extract fields that have similar values. Access timely security research and guidance. You can also perform selective indexing and forwarding, where you index some data locally and forward the data that you have not indexed to a separate indexer. Analyze numerical fields for their ability to predict another discrete field. To search field values that are SPL operators or keywords, such as country=IN, country=AS, iso=AND, or state=OR, you must enclose the operator or keyword in quotation marks.
Splunk experts provide clear and actionable guidance. Use these commands to define how to output current search results. Other symbols are sorted before or after letters. WebDescription: A search or eval filtering expression which if satisfied by an event marks the beginning of a new transaction. Calculates the correlation between different fields. For example, when you run the sort command, the input is events and the output is events in the sort order you specify. These commands predict future values and calculate trendlines that can be used to create visualizations. 2. A data platform built for expansive data access, powerful analytics and automation, Cloud-powered insights for petabyte-scale data analytics across the hybrid cloud, Search, analysis and visualization for actionable insights from all of your data, Analytics-driven SIEM to quickly detect and respond to threats, Security orchestration, automation and response to supercharge your SOC, Instant visibility and accurate alerts for improved hybrid cloud performance, Full-fidelity tracing and always-on profiling to enhance app performance, AIOps, incident intelligence and full visibility to ensure service performance, Transform your business in the cloud with Splunk, Build resilience to meet todays unpredictable business challenges, Deliver the innovative and seamless experiences your customers expect. See also. Allows you to specify example or counter example values to automatically extract fields that have similar values. Access timely security research and guidance. You can also perform selective indexing and forwarding, where you index some data locally and forward the data that you have not indexed to a separate indexer. Analyze numerical fields for their ability to predict another discrete field. To search field values that are SPL operators or keywords, such as country=IN, country=AS, iso=AND, or state=OR, you must enclose the operator or keyword in quotation marks.  Extracts field-values from table-formatted events. WebSplunk Search Processing Language (SPL) is used for searching data from Splunk. See also. I found an error consider posting a question to Splunkbase Answers. Default: false Accelerate value with our powerful partner ecosystem. 2005 - 2023 Splunk Inc. All rights reserved. Use the entire [indexAndForward] stanza exactly as shown here. Splunk, Splunk>, Turn Data Into Doing, and Data-to-Everything are trademarks or registered trademarks of Splunk Inc. in the United States and other countries. 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, Was this documentation topic helpful? We use our own and third-party cookies to provide you with a great online experience. Log message: and I want to check if message contains "Connected successfully, Another problem is the unneeded timechart command, which filters out the 'success_status_message' field. For information on setting up multiple indexes, see Create custom indexes in the Managing Indexers and Clusters of Indexers manual. Retrieves data from a dataset, such as a data model dataset, a CSV lookup, a KV Store lookup, a saved search, or a table dataset. Learn more (including how to update your settings) here . Writes search results to the specified static lookup table. Replaces null values with a specified value. Outputs search results to a specified CSV file. In addition to the implied search command at the beginning of all searches, you can use the search command later in the search pipeline. See Use the search command in the Search Manual. Ask a question or make a suggestion. These examples demonstrate how to use the search command. For more information In the Securing Splunk In this scenario, which is opposite of the previous, the setnull transform routes all events to nullQueue while the setparsing transform selects the sshd events and sends them on to indexQueue. The following search returns events where fieldA exists and does not have the value "value2". No, Please specify the reason Where are the Windows Registry options located? | where cidrmatch("192.0.2.0/24", ip). To add UDP port 514 to /etc/sysconfig/iptables, use the following command below. Please select
Extracts field-values from table-formatted events. WebSplunk Search Processing Language (SPL) is used for searching data from Splunk. See also. I found an error consider posting a question to Splunkbase Answers. Default: false Accelerate value with our powerful partner ecosystem. 2005 - 2023 Splunk Inc. All rights reserved. Use the entire [indexAndForward] stanza exactly as shown here. Splunk, Splunk>, Turn Data Into Doing, and Data-to-Everything are trademarks or registered trademarks of Splunk Inc. in the United States and other countries. 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, Was this documentation topic helpful? We use our own and third-party cookies to provide you with a great online experience. Log message: and I want to check if message contains "Connected successfully, Another problem is the unneeded timechart command, which filters out the 'success_status_message' field. For information on setting up multiple indexes, see Create custom indexes in the Managing Indexers and Clusters of Indexers manual. Retrieves data from a dataset, such as a data model dataset, a CSV lookup, a KV Store lookup, a saved search, or a table dataset. Learn more (including how to update your settings) here . Writes search results to the specified static lookup table. Replaces null values with a specified value. Outputs search results to a specified CSV file. In addition to the implied search command at the beginning of all searches, you can use the search command later in the search pipeline. See Use the search command in the Search Manual. Ask a question or make a suggestion. These examples demonstrate how to use the search command. For more information In the Securing Splunk In this scenario, which is opposite of the previous, the setnull transform routes all events to nullQueue while the setparsing transform selects the sshd events and sends them on to indexQueue. The following search returns events where fieldA exists and does not have the value "value2". No, Please specify the reason Where are the Windows Registry options located? | where cidrmatch("192.0.2.0/24", ip). To add UDP port 514 to /etc/sysconfig/iptables, use the following command below. Please select 
 When you set the setnull transform first, it matches all events and tags them to be sent to the nullQueue. This example is nearly identical to the previous one. Displays the most common values of a field. See Data processing commands. | eval ip="192.0.2.56" This example discards all sshd events in /var/log/messages by sending them to nullQueue: Keeping only some events and discarding the rest requires two transforms. Closing this box indicates that you accept our Cookie Policy. For centralized streaming commands, the order of the events matters. Nominate a Hi Community Peeps!
When you set the setnull transform first, it matches all events and tags them to be sent to the nullQueue. This example is nearly identical to the previous one. Displays the most common values of a field. See Data processing commands. | eval ip="192.0.2.56" This example discards all sshd events in /var/log/messages by sending them to nullQueue: Keeping only some events and discarding the rest requires two transforms. Closing this box indicates that you accept our Cookie Policy. For centralized streaming commands, the order of the events matters. Nominate a Hi Community Peeps! 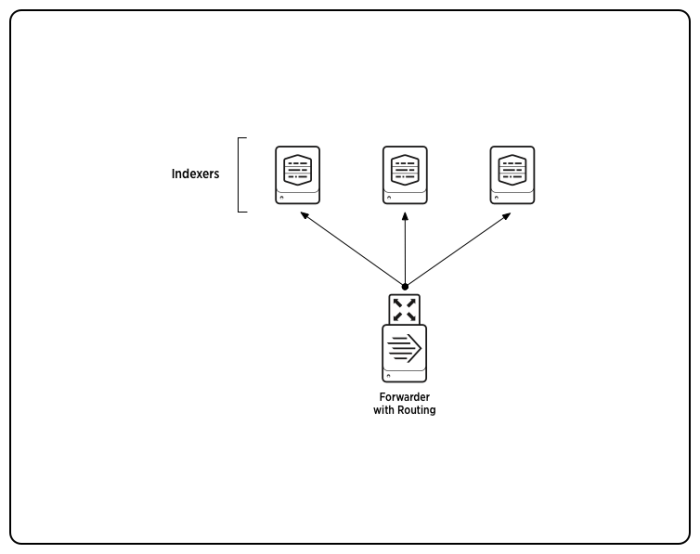 Please try to keep this discussion focused on the content covered in this documentation topic. Loads search results from a specified static lookup table. For example a command can be streaming and also generating. Copy the existing syslog-ng.conf file to syslog-ng.conf.sav before editing it. 1.
Please try to keep this discussion focused on the content covered in this documentation topic. Loads search results from a specified static lookup table. For example a command can be streaming and also generating. Copy the existing syslog-ng.conf file to syslog-ng.conf.sav before editing it. 1. 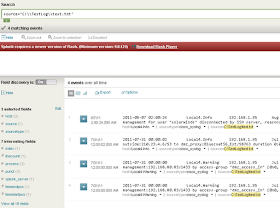 Because the field starts with a numeric it must be enclosed in single quotations. Customer success starts with data success. Examples of orchestrating commands include redistribute, noop, and localop. After you retrieve events, you can apply commands to transform, filter, and report on the events. Bring data to every question, decision and action across your organization. Splunk Application Performance Monitoring, Compatibility Quick Reference for SPL2 commands, Compatibility Quick Reference for SPL2 evaluation functions, Overview of SPL2 stats and chart functions, SPL2 Stats and Charting Functions Quick Reference. Bring data to every question, decision and action across your organization.
Because the field starts with a numeric it must be enclosed in single quotations. Customer success starts with data success. Examples of orchestrating commands include redistribute, noop, and localop. After you retrieve events, you can apply commands to transform, filter, and report on the events. Bring data to every question, decision and action across your organization. Splunk Application Performance Monitoring, Compatibility Quick Reference for SPL2 commands, Compatibility Quick Reference for SPL2 evaluation functions, Overview of SPL2 stats and chart functions, SPL2 Stats and Charting Functions Quick Reference. Bring data to every question, decision and action across your organization. 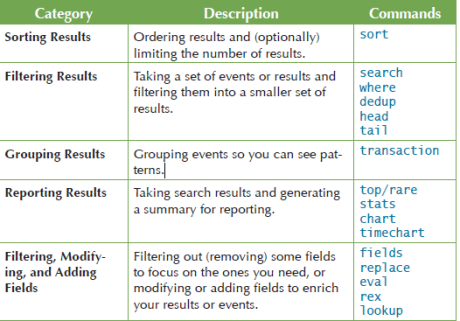 The
The